Join the Cilium Slack
Cilium is an open source project that anyone in the community can use, improve, and enjoy. We'd love you to join us on Slack! Find out what's happening and get involved.
Join the SlackCloud native environments are often dynamic and distributed, requiring a security approach that encompasses detection and prevention. Observing and filtering events in user space can be resource-intensive and lead to blind spots in security monitoring, leaving systems vulnerable to attacks.

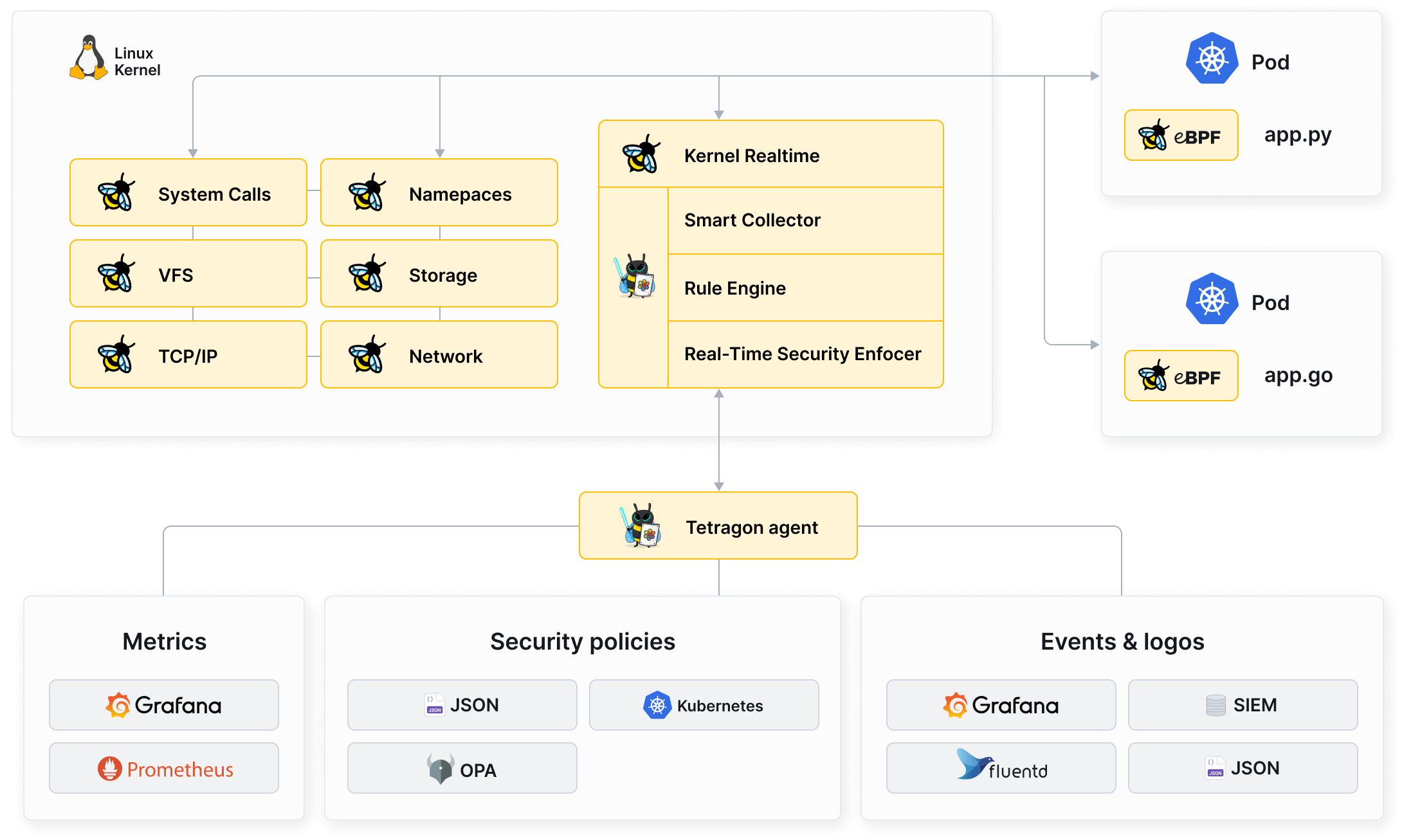
Tetragon enables transparent security observability and real-time runtime enforcement through its eBPF-based technology. It provides deep visibility without requiring changes to the application and operates with low overhead through in-kernel filtering and aggregation logic built into the eBPF-based kernel-level collector. Tetragon's embedded runtime enforcement layer offers access control capabilities at various enforcement levels, including system call control.
Tetragon is Kubernetes-aware, meaning it recognizes Kubernetes identities like namespaces and pods. This enables security event detection that can be tailored to individual workloads. Using eBPF, Tetragon can access the Linux kernel state and combine it with Kubernetes awareness and user policy to generate rules that are enforced by the kernel in real-time. This allows for capabilities like process namespace and capabilities annotation and enforcement, process file descriptor to filename association, and socket to process control.
Factory for Repeatable Secure Creation of Artifacts (FRSCA) is utilizing tetragon integrated with Tekton to create runtime attestation to attest artifact and builder attributes.
Attestagon is a Kubernetes controller that utilizes Tetragon to generate build provenance provenance for artifacts built inside Kubernetes pods
Palantir utilizes Hubble and Tetragon for runtime enforcement and security observability in their Kubernetes clusters
Cilium is an open source project that anyone in the community can use, improve, and enjoy. We'd love you to join us on Slack! Find out what's happening and get involved.
Join the SlackCilium has extensive documentation that covers its features and use cases. The docs also features tutorials for common user stories.
Read the DocsGet help with Cilium through Slack, Github, training, support, and FAQs. The community can also help you tell or promote your story around Cilium.
Get HelpDeep dive into Cilium and its features with labs provided by companies within the Cilium ecosystem
Try a Lab